
&
Author: Charlotte Gifford
August 20, 2020
To the outside world, Kim Hyon Woo was a developer working for Chosun Expo Joint Venture, a China-based company that supplies freelancing software development and gambling-related products. But in reality, Kim didn’t exist. The person who controlled his email accounts – a man named Park Jin Hyok – was born and educated in North Korea.
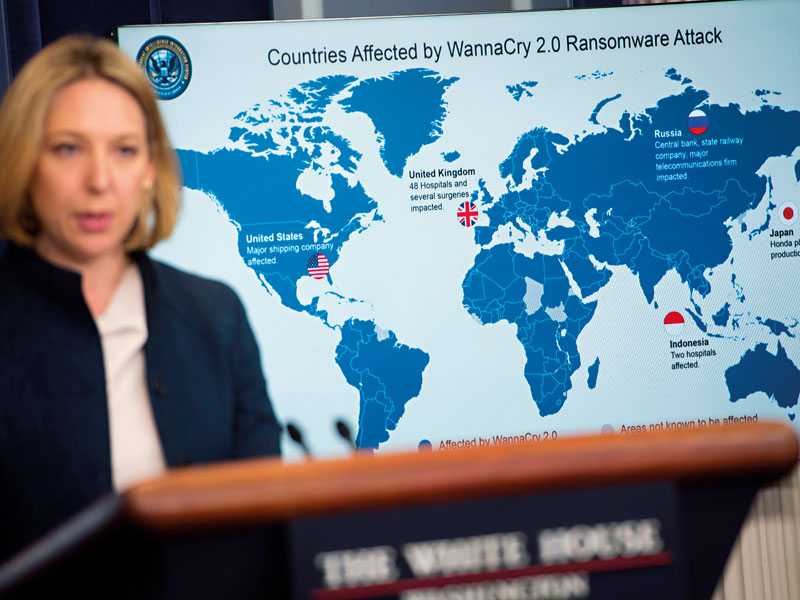
Chosun Expo was also not what it seemed. As a matter of fact, it was a front company for Lab 110, a top-secret arm of the Democratic People’s Republic of Korea’s (DPRK’s) military intelligence agency. When Chosun Expo wasn’t carrying out normal business operations, it was facilitating some of the world’s highest-profile cyberattacks, including the Sony Pictures hack of 2014 and the WannaCry ransomware attack of 2017, the latter of which affected more than 200,000 systems across 150 countries and crippled hospitals in the UK, ultimately costing the National Health Service £92m ($117.3m).
It’s estimated that the value of attempted cyber heists conducted by Park and his co-conspirators between 2015 and 2018 amounted to $1bn. Eventually, connections to Kim’s email addresses revealed Park to the FBI. “The scope and damage of the computer intrusions perpetrated and caused by the subjects of this investigation, including Park, is virtually unparalleled,” Nathan P Shields, a special agent with the FBI, concluded at Park’s trial.
The WannaCry hack was one of the costliest cyberattacks in history, but represented just one of the numerous incidents that alerted the international community to the growing sophistication of North Korea’s hackers. Now, recent reports indicate that cyberattacks have become more than a form of warfare for North Korea: they are also a key source of income for Kim Jong-un’s brutal regime.
A money-spinner
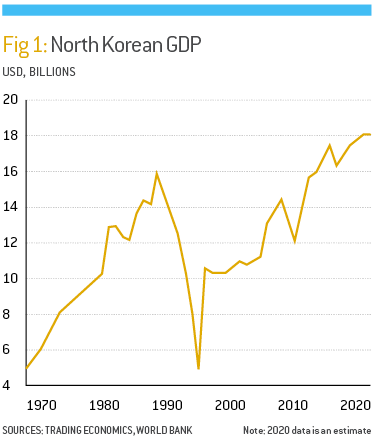
According to a report presented to the UN Security Council Sanctions Committee on North Korea, the authoritarian state generated approximately $2bn from cyberattacks between 2016 and 2019 – a significant amount, considering the country’s GDP was worth an estimated $18bn in 2019 (see Fig 1). These funds were subsequently funnelled into the DPRK’s military.
“The US Government has released reports affirming that the funds are being spent on weapons of mass destruction and ballistic missiles programmes,” Kathryn Waldron, a fellow at the R Street Institute who focuses on cybersecurity, told World Finance. “Experts have also speculated that some of the funds may go to supporting the Kim family’s opulent lifestyle, as well as other government programmes.”

North Korea has a long history of bringing capital into the country via illicit means. Since the 1970s, the country has engaged in the manufacturing, selling and trafficking of drugs such as methamphetamine – not to mention the production of counterfeit currency. According to the Congressional Research Service, a dollar-counterfeiting operation made North Korea about $15m per year at its peak.
Many academics hold that these operations have long been a core revenue stream for the state, with Robert Collins, Bruce Bechtol and Paul Rexton Kan calling the regime’s practices a form of “criminal sovereignty” in their book of the same name. Cybercrime is the latest of these moneymaking endeavours, and the UN’s report suggests it could become the most financially lucrative so far.
But this was not always the case: not long ago, analysts scoffed at North Korea’s cyber capabilities. Its distributed denial-of-service (DDoS) attacks in 2009 only temporarily shut down South Korean websites and ultimately did little damage. Attacks like this were ideologically motivated and primarily intended as acts of cyber warfare. It’s only in recent years that the nation has begun harnessing its cyber capabilities with the specific intention of generating funds.
“Right now, most of their attention seems to be on using the full range of what is possible in cyberspace to generate as much foreign currency as possible,” Jenny Jun, a PhD student in the Department of Political Science at Columbia University, told World Finance. In September 2018, cybersecurity research firm FireEye uncovered the existence of a specific unit in North Korea’s cybercrime group – Lazarus Group – that seemed to be dedicated specifically to financial crime. This same group was behind the Bangladesh Bank cyber heist of 2016, which saw at least $81m stolen by North Korean actors. In the same attack, North Korea came within a hair’s breadth of stealing $1bn from the US Federal Reserve – the only reason it didn’t succeed was that the bank spotted a spelling mistake in one of the transactions.
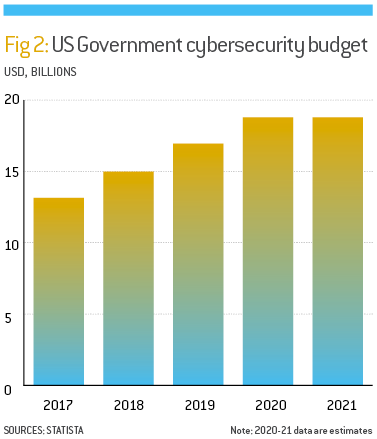

Today, there are myriad ways that North Korea uses its cyber operations to generate revenue beyond attacks on financial institutions. “[North Korean] cyber activity includes everything from stealing from cryptocurrency exchanges, fraudulent SWIFT transactions [and] ransomware [to] blackmail with exfiltrated data, ‘cryptojacking’ and hackers for hire,” Jun explained. As North Korea’s cyber heists have become more sophisticated and costly, the international community has raised its threat level and response, especially the US (see Fig 2). In April, the US Government announced it was offering $5m for information on hackers – an unusual step for the nation and a sign that the cyberthreat posed by North Korea is now widely recognised on the international stage.
“North Korean hackers pose a serious threat to the global financial system,” Waldron said. “We’ve seen North Korean hackers engaged in a wide variety of malicious cyber activity within the global financial system, including holding data for ransom, stealing cryptocurrency and even using malware to make fraudulent ATM withdrawals.”
Dodging sanctions
North Korea’s cyber prowess may seem improbable for one of the poorest and most cut-off countries in the world, where only the elite have access to the internet, but analysts believe it has finessed a formula for recruiting young cyber prodigies. “It is believed that students showing potential are selected at a young age, around middle school, to enter into a special training programme,” Jun explained.
Cyberattacks have become more than a form of warfare for North Korea: they are also a key source of income
The state then funnels them into one of two universities: either Pyongyang’s Kim Il-sung University or Kim Chaek University of Technology. After this, they are sent abroad to Russia or China to strengthen their knowledge of hacking. Broadband is generally cheaper and faster in these countries, which helps North Korea overcome the problem of limited internet access.
North Korea’s hacking elite are well compensated for their training. In addition to receiving food subsidies and a generous stipend for overseas deployments, hackers and their families get the privilege of living in the capital, Pyongyang. Although cybercrime may seem an unlikely mode of operating for the isolated nation, in other respects, it presents itself as the ideal income generator: for one, it’s low-cost. Further, with North Korea far from being fully integrated into the global internet infrastructure, the country is surprisingly invulnerable to retaliation. Cybercrime also softens the economic blow of North Korea’s exclusion from the global financial system: without sufficient income from trade, illicit cyber activities become a vital stream of wealth for the state and enable North Korea to evade international sanctions.


The state has faced multilateral sanctions from the UN ever since 2006, when North Korea carried out its first nuclear test. Initially, these sanctions focused mainly on weapons-related goods, but gradually they were expanded to include luxury goods to target the elite. For the first decade, sanctions were thought to have little impact on North Korea. But since 2016, US President Donald Trump has championed a “maximum pressure” campaign that places caps on energy imports, bans exports of minerals and textiles, and prohibits the granting of new permits for overseas North Korean workers. Although it’s difficult to measure the exact impact of these sanctions, given how limited North Korea’s economic data is, the Bank of Korea in Seoul estimates that the state’s annual GDP fell by 3.5 percent in 2017 as a result.
North Korea has always sought to dodge sanctions using its smuggling networks. In 2017, the DPRK earned about $200m from banned exports of coal and arms, according to a secret report by independent UN observers. The UN also claimed that it was thanks to a covert shipping network that North Korea avoided gasoline and diesel fuel shortages in 2019. More recently, North Korea has used cryptocurrency to fund these illicit trade networks.


By any means necessary
The use of virtual tokens like bitcoin makes the movement of money and goods across borders much harder to detect. “Cryptocurrencies enable North Korea to carry out illicit [activities], primarily because [these coins], by nature, are used outside of the formal financial system,” Kayla Izenman, a research analyst at the Royal United Services Institute’s Centre for Financial Crime and Security Studies, told World Finance. “This means that North Korea avoids interacting with financial institutions, [which] are quite advanced in tracking illicit activities, and instead either bypasses centralised intermediaries (such as cryptocurrency exchanges) entirely or uses ones with low or no compliance processes in place.”


In March 2019, a UN panel estimated that North Korea had amassed $670m in virtual and fiat currency – largely by stealing it. Although North Korea denies such activities, it is widely thought to have successfully targeted Asian cryptocurrency exchanges at least five times from January 2017 to September 2018, with losses from these exchanges estimated at $571m.
Izenman believes North Korea’s success in hacking these exchanges indicates a need for more robust security measures: “Despite progress in international cryptocurrency industry regulation and even proactive compliance measures adopted by some exchanges in advance of required regulation in their jurisdictions, some exchanges still do not require much, if any, information on their customers. North Korea has been known to use these exchanges and sometimes even use fake IDs to bypass lax customer due diligence procedures.”
The state’s success in attacking these institutions and exchanges is also a testament to its growing sophistication as a hacking power. “In little over a decade, North Korea has significantly increased its cyber operations capacity [and] diversified its targets, [while] its tools, techniques and procedures have become more sophisticated,” Jun said. “Back in 2009, when North Korea was just beginning to operate in this space, they were doing relatively simple DDoS attacks against foreign websites… By 2014, North Korean advanced persistent threat groups had demonstrated that they have the organisational and technical capacity to compromise and gain admin privileges on a network such as Sony, maintain a persistent presence, demonstrate some creative ways to conduct socially engineered phishing and, finally, understand how to use cyber capabilities to have the most damaging effect on a target.”
However, Jun pointed out that North Korean cyberattacks are still far from flawlessly executed: “Details behind the WannaCry ransomware [attack] also show that they are sometimes sloppy too if the real goal has been indeed to generate revenue and not for disruptive reasons.” For example, the malware used only four hardcoded bitcoin addresses, making it easier for the security community and law enforcement to track any attempt to anonymously cash out WannaCry profits. What’s more, despite the huge amount of damage it inflicted on transport and healthcare systems, the ransomware only made the hackers around $55,000.
But weaknesses in North Korea’s hacking strategy are not necessarily cause for celebration: for every cyberattack that isn’t perfectly executed, one can assume the next will be an improvement.

A global threat
As North Korean cyber capabilities have grown in sophistication, countries have become more aware of the havoc they could potentially wreak. In an advisory released in April 2020, US officials said that North Korea’s cyber activity poses “a significant threat to the integrity and stability of the international financial system”.
For every cyberattack that isn’t perfectly executed by North Korea, one can assume the next will be an improvement
“I think there’s been a distinct shift in [the] global understanding of North Korea’s cyber power, probably following the Sony hack in 2014 and really increasing in awareness after WannaCry in 2017,” Izenman said. “I’ve found states are generally aware of North Korea’s hacking prowess, but perhaps less aware of the way in which this directly connects to their proliferation financing model. And if they do understand the connection between cyber and financing the regime, they often focus on bank or ATM hacks and don’t realise how much North Korea is gaining in cryptocurrency.”
Some analysts have argued that North Korea’s exclusion from the financial system motivates it to create economic chaos for the rest of the world, but Jun disagrees with this view: “Although I think North Korea has considerable intent and capacity to target financial institutions for monetary gain, I don’t think it is necessarily in their interest to paralyse the global financial system for destructive purposes. They don’t want to kill the chicken that continues to lay eggs.”
Although it may not be North Korea’s intention to deliberately undermine the financial system, this could be an indirect consequence of its more devastating attacks. If the state succeeded in attacking a major financial institution, for example, it could undermine its ability to lend, potentially triggering a financial crisis.
“Events like the Bangladesh Bank heist show that fraudulent SWIFT transactions can be made – which other criminal groups such as Carbanak have also been doing – and more news about such vulnerabilities that can be exploited can lower consumer confidence,” Jun explained. “There is also a broader policy question concerning regulation and oversight over international cryptocurrency transactions.”
North Korea’s exclusion from the financial system motivates it to create economic chaos for the rest of the world
Waldron, meanwhile, warns that the threat from North Korean hackers may be greater now than ever before: “With the global economy reeling from the economic impact of COVID-19, governments, businesses and financial institutions are uniquely vulnerable to the financial costs of a successful cyberattack. And COVID-19 has presented hackers with new cybersecurity vulnerabilities to exploit.
“In many countries, a greater number of government and business employees are working from home. This presents North Korean hackers with particularly vulnerable targets, as many of these employees may not be well versed in cybersecurity. North Korean hackers have also used COVID-19-related material as a trap for unsuspecting victims, such as when they emailed South Korean government officials documents detailing COVID-19 response plans laced with malware.”
Although the international community is now largely in agreement that North Korean cyber activity poses a serious threat, it remains unclear what it should do about it. Sanctions would have little effect – so far, North Korea’s economic isolation has only exacerbated its need for illicit income. “If North Korea secures a steady stream of foreign cash that can be funnelled back into its nuclear and missile programme… the sanctions regime [is neither] effectively going to slow this process nor act as a punishment mechanism to persuade North Korea to denuclearise,” Jun said. “This may alter bargaining dynamics at the negotiation table.”
Negotiation is particularly difficult when the perpetrator refuses to own up to their crimes. When the US issued its warning on the North Korean cyberthreat in April, North Korea feigned ignorance. “We want to make it clear that our country has nothing to do with the so-called ‘cyberthreat’ that the US is talking about,” North Korea’s Foreign Ministry said in a statement. Similarly, when Park was charged, North Korea not only denied his crimes but also called him a “non-existent entity”.
As long as its cyber programme remains financially lucrative, the North Korean state has no reason to admit to its actions. For now, the international community is left with little option but to simply stay vigilant and invest in defences against this growing threat.
